1. World of Peacecraft / Realistic


I navigated to the inbox to check for relevant emails. I identified an email titled “World of Peacecraft — Activate Account” and opened it
I saw a message directing the user to a specific website in order to activate their account so I kept a record of the given URL since I figured I’ll be needing it later to activate the account.
I Navigated to the trash folder within the email account. I Looked for any discarded emails that may contain valuable information. I was able to identify an email titled “uStudio — Password Request” and I opened it.


I returned to the “World of Peacecraft — Activate Account” email. I clicked on the provided link, which took me to a page prompting for the password.


2. Library Gateway / Realistic


I modified the URL, “https://defendtheweb.net/extras/playground/real/2/members” It opened a new page associated with the provided login credentials.


3. Princess slag / Realistic





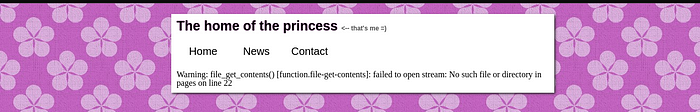
I decided to modify the URL by replacing a part of it. I tried changing the URL to “https://defendtheweb.net/extras/playground/princess-slag/?p=%00".



4. Xmas ’08 / Realistic







To achieve the objective of replacing the original homepage, I deleted the existing code within the editor. Next, I copied the source code from the ‘Alternative Homepage’ provided in the CTF challenge and paste it into the editor. Finally, I saved the changes.


Thank you so much for reading my writeup!
Don’t forget to share, follow and leave a comment.
